Deposits API
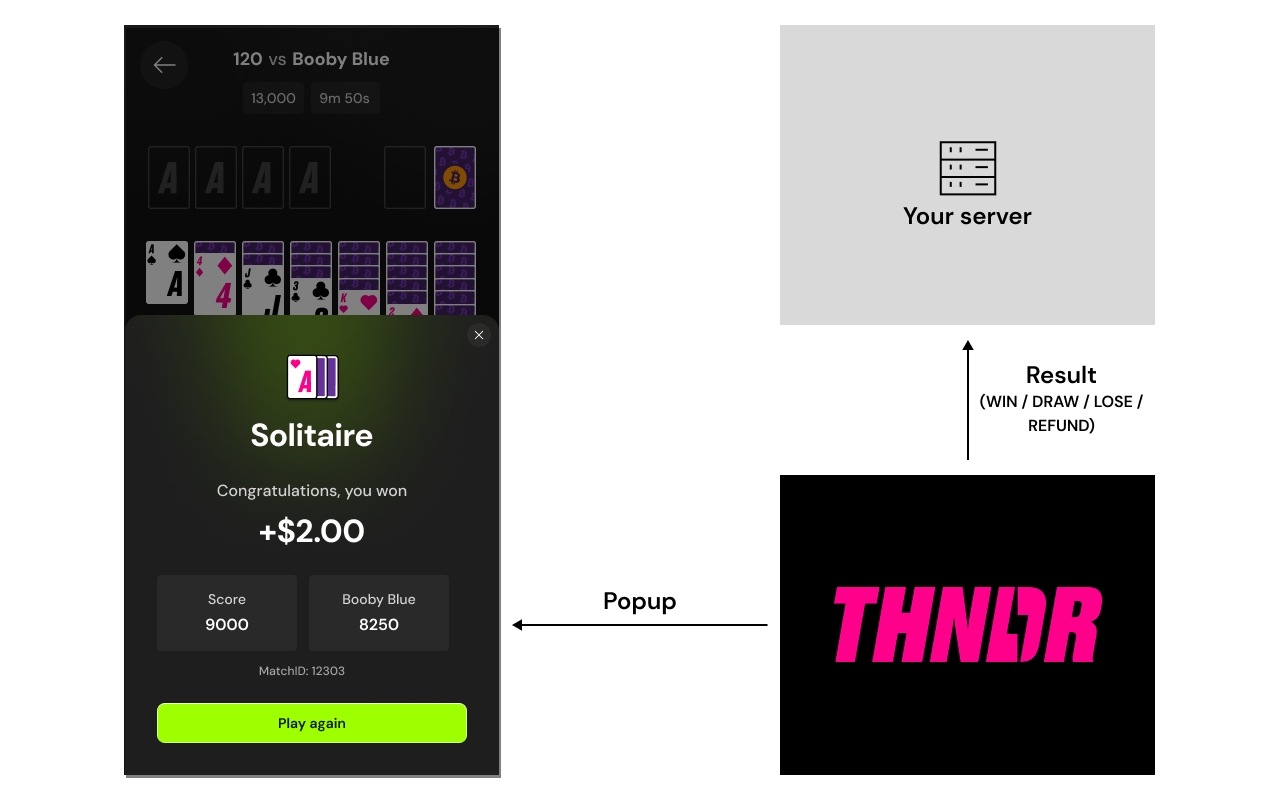
Server to Server Callbacks
To receive messages on when to deduct and credit user balances based on the outcomes of matches, you should implement the following endpoints.
Pay Entry Fee
Method: POST /thndr/pay
Description: When you receive this post request from us:
Deduct the bet amount from the user's balance.
Associate the
depositIdwith theamountin your database to allow for potential refunds.Use
depositIdas the idempotency key to ensure the same payment is not processed twice.
Body:
{
"userId": "123",
"depositId": "abc",
"currency": "USD",
"amount": 50
}
Payment Errors
If you need to notify your client about any payment errors, such as "Insufficient Balance", you can return errors in the response with a status code 4XX. These errors will be sent to the client sdk via the handleError callback for your front end to handle.
Note: You must pass "isClientSafe": true in the response for it to be passed to the client.
Example 4XX response:
Handle Match Results
Method: POST /thndr/results
Description: Upon receiving this POST request from us, take the appropriate action based on the match outcome:
WIN or DRAW: Credit the user's balance by
amount.LOSE: No action required.
REFUND: Retrieve the
amountfrom your database and refund the user.
Note: Use depositId as the idempotency key to ensure the same result is not processed twice.
Important: If a system crash occurs before receiving a response from the /thndr/pay webhook, you may receive refund requests for deposit IDs that were never persisted in your database (i.e., the user was not credited). These requests must be ignored, and a 200 status code must be returned.
Body (WIN or DRAW):
Body (LOSE):
Body (REFUND):
Request Signing
To ensure the integrity and authenticity of API requests, our system signs each request payload using an HMAC (Hash-based Message Authentication Code) with the SHA-256 algorithm. Integrators must verify the signature to authenticate requests and prevent tampering.
Verification Process
To verify the request's authenticity, the integrator should:
Recompute the signature using the shared secret and the received payload.
Compare the computed signature with the
x-server-authorizationheader value.Reject the request if the signatures do not match.
Example Verification in Node.js:
The SERVER_SECRET is a pre-shared secret key known only to THNDR server and the integrator.
Example Signed Payload
Last updated